Key Takeaways:
- Attackers don’t just fire off random emails. They often research the target and its suppliers extensively.
- Spoofed emails often mimic legitimate addresses with only subtle changes that are easy to miss.
- Victims can feel pressured to respond quickly without double-checking. Take your time, review and check before you act.
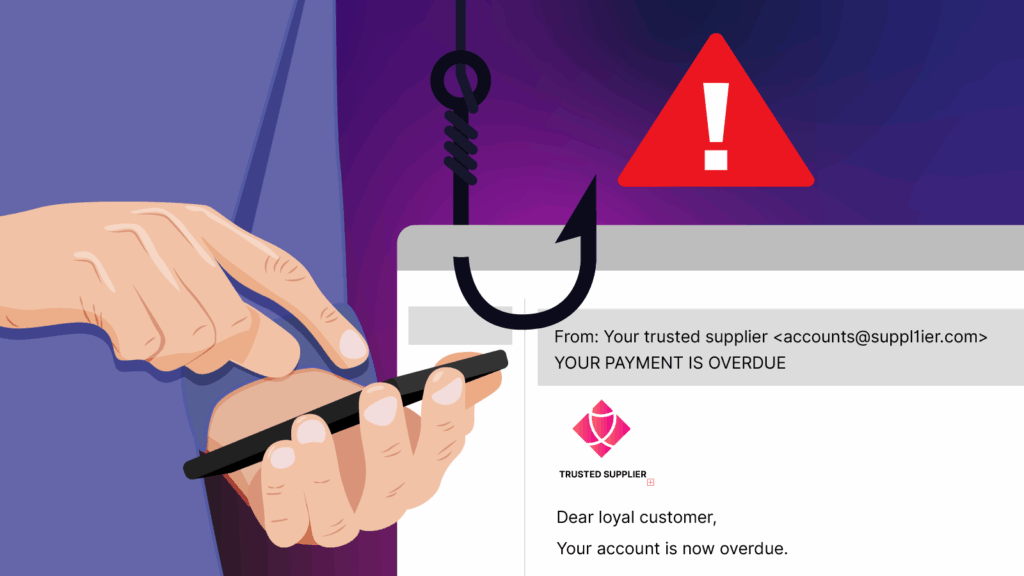
Imagine if your stationery supplier, bookkeeper, caterer weren’t who you thought they were? They’ve sent you an email requesting payment, but it was actually from a cyber criminal.
You might have stumbled upon a case of vendor spoofing. And it’s no laughing matter. Small businesses rely on their vendors and suppliers every day to keep their operations running smoothly, but attackers have found a way to exploit that trust. And it can be a costly headache.
What is vendor spoofing?
Vendor spoofing is a cyber attack in which criminals impersonate a trusted third-party vendor or supplier. The goal is to trick organisations into making unauthorised payments, sharing sensitive information, or installing malware.

Attackers don’t just fire off random emails. They often research the target and its suppliers extensively, gathering enough detail to create convincing and highly tailored messages.
Why does vendor spoofing work?
Vendor spoofing is effective at its core because it plays on trust and familiarity. Employees are used to processing invoices or vendor requests, and this routine can lower their guard.
Spoofed emails often mimic legitimate addresses with only subtle changes that are easy to miss. Add a sense of urgency, like overdue payment demands, and victims can feel pressured to respond quickly without double-checking.
How to spot a vendor spoofing attempt
While these scams are sophisticated, there are red flags to look out for:
- Slight variations in the sender’s email address
- Unexpected payment instructions or sudden changes to bank details
- Poor grammar, awkward phrasing, or unusual tone in messages
- Requests designed to bypass normal payment or approval workflows
- Urgent demands or threats of service disruption
Protecting your business from vendor spoofing
Verify changes:
Always confirm updated vendor details using a trusted communication channel. For example, if you receive a suspicious invoice, don’t call the number on the invoice; it might lead to the cyber criminals. Instead, find your supplier’s phone number on their website or your phone contacts.
Audit vendors:
Maintain accurate and up-to-date relationships and databases.
Strengthen authentication:
Utilise multi-factor authentication across systems, especially for financial processes.
Match invoices:
Reconcile invoices against purchase orders before approving payments to ensure accuracy.
Train staff:
Ensure employees complete the Cyber Wardens course to stay alert to emerging threats.
Vendor spoofing reminds us that cyber criminals can weaponise even routine business interactions. By combining the right technology, strong processes, and ongoing awareness training, organisations can significantly reduce their exposure to this growing threat.
For more tips on keeping your business safe from these scams, enrol in the free Cyber Wardens training program.