You trust the people you work with. You recognise their names, their voices, their writing style and even the way they sign off emails. Cyber criminals know this, and they’re exploiting it using AI-created digital doppelgängers. These convincing online clones are being used to impersonate real people, trick businesses into handing over money or sensitive information, and bypass even the most well-trained employees.
Key Takeaways:
- AI-powered impersonation is on the rise. Digital doppelgängers use deepfakes and publicly available information to convincingly impersonate real people online, making scams harder to spot.
- Familiar faces can still be fake. Cyber criminals rely on trust and urgency to bypass suspicion, even among well-trained employees and businesses.
- Simple checks can stop serious damage. Education, multi-factor authentication and verifying unusual requests through a second channel can significantly reduce the risk.
What is a digital doppelgänger?
A digital doppelgänger is a cloned online identity designed to look, sound and act like a real person. It’s a carefully crafted persona that mimics the details of a genuine individual, often so closely that it’s difficult to tell the difference.
These fake identities are commonly built using publicly available information, such as social media profiles and company websites, combined with deepfake technology and details gathered from phishing or previous data breaches. The result is an online presence that feels familiar and believable.
How digital doppelgängers are being used
Cyber criminals are using these clones in several common scams.
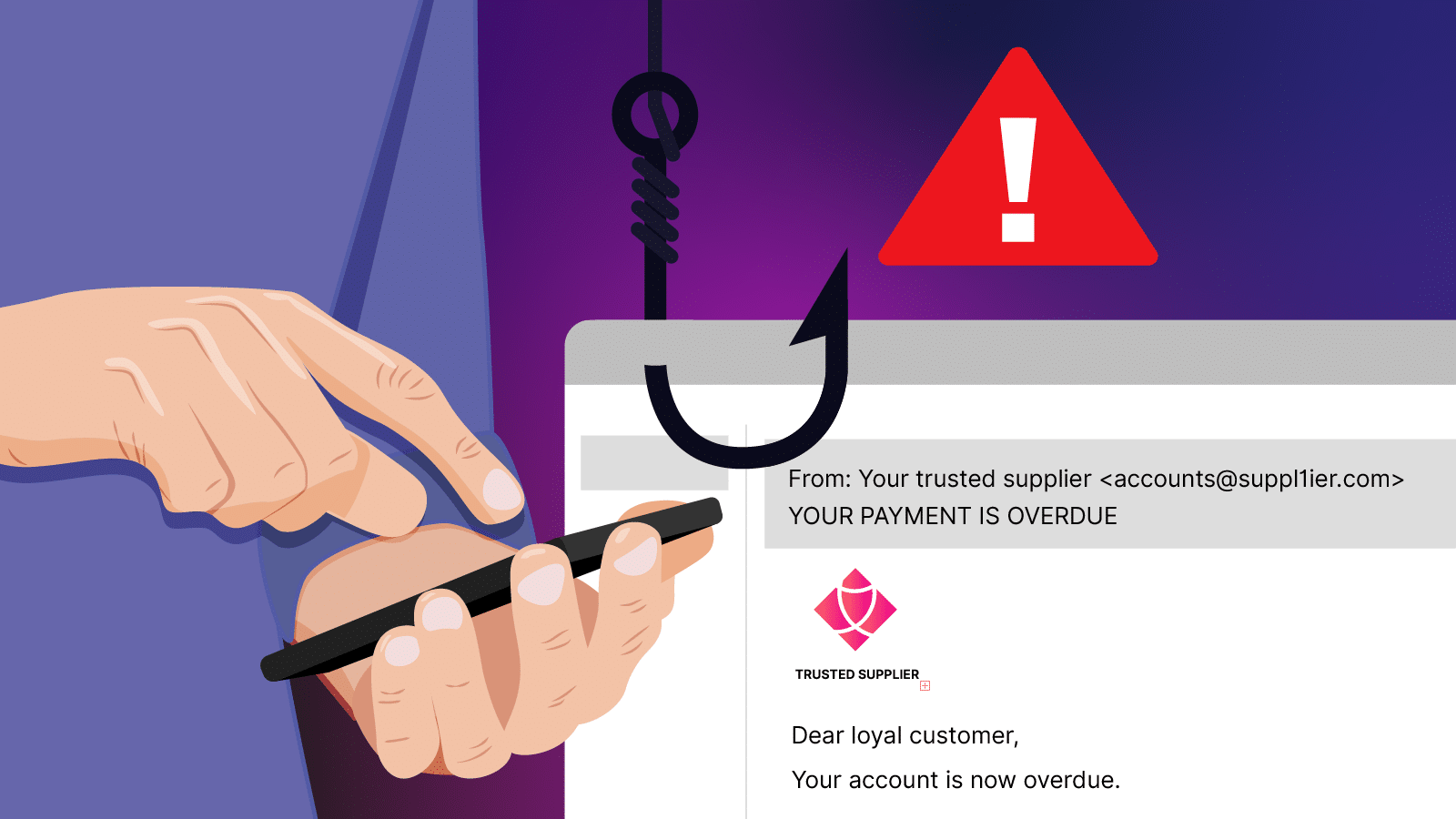
In business email compromise attacks, scammers pose as executives or employees and send urgent requests for payments or sensitive information. Because the email looks and sounds right, it can slip through without raising alarms.
In social engineering and vishing scams, deepfake voice technology is used to impersonate CEOs or managers over the phone. Victims are pressured into sharing information or approving payments that seem legitimate.
Digital doppelgängers are also used for credential harvesting. Fake social media profiles or messages lure people into clicking malicious links, downloading malware, or logging in to convincing fake websites designed to steal passwords.
In some cases, clones are used for reputation sabotage, posting false or damaging content under a real person’s name to harm credibility or manipulate public opinion.

Why these scams work
Humans are wired to trust familiarity. When a message appears to come from someone you know, especially a senior colleague, your guard naturally drops.
Add urgency into the mix, such as a tight deadline or a ‘quick favour,’ and even cautious employees can be manipulated into acting before they have time to question what’s happening.
How you can protect yourself and your business
Awareness is your first line of defence. Ensure your team is aware that digital impersonation is a possibility and is becoming increasingly common.
Use multi-factor authentication wherever possible to reduce the damage if login details are compromised.
Limit the amount of personal and professional information shared publicly online, particularly details about roles, reporting lines and contact information.
Invest in verification processes and tools, and encourage staff to confirm unusual requests through a second channel, such as a phone call or in-person check.
Checklist
If something feels off, pause
As deepfake technology evolves, spotting fakes is becoming harder. But simple habits can still make a big difference.
- Stop and take a moment if something doesn’t feel quite right.
- Check by verifying the request through another method.
- Protect your data by following your organisation’s security processes.
Conclusion
Trust is important but verification is essential. For more guidance, enrol in the Cyber Wardens training program today.