The tourism industry is a cyber criminal’s dream destination. With its reliance on technology, continuous financial transactions, and large volumes of sensitive customer data, it’s no wonder small tourism businesses are increasingly targeted by cyber threats. And the risks are evolving daily, from phishing attacks to data breaches.
What do cyber threats look like for the tourism industry?
Small tourism businesses are uniquely vulnerable to a range of cyber threats that exploit sensitive data, financial transactions, and digital systems. Here are some of the most common threats, and how they’ve impacted businesses like yours.
Data breaches and data theft
Tourism businesses store vast amounts of sensitive data, from customer records to financial details. A breach can lead to secondary attacks and long-term reputational damage. For example, Melbourne-based travel agency Inspiring Vacations exposed over 112,000 customer records by leaving an Amazon AWS cloud storage bucket unsecured. Similarly, Ticketek suffered a cyber incident in which customer personal information—including names, dates of birth, and email addresses—was potentially exposed due to a third-party cloud platform vulnerability.
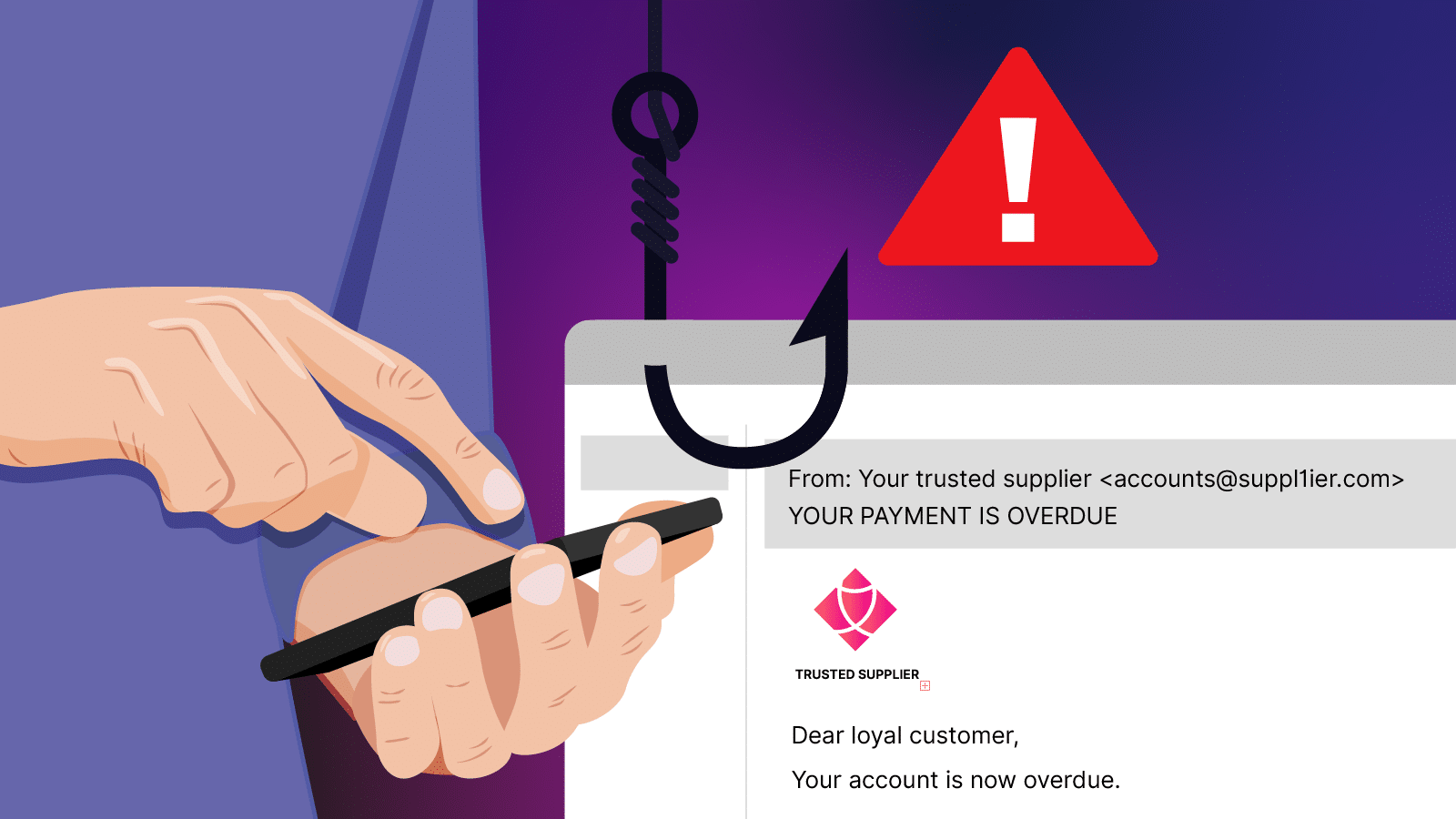
Phishing attacks
Phishing scams use deceptive emails to trick recipients into revealing sensitive information or clicking malicious links. During the CrowdStrike outage in 2024, scammers impersonated airline customer service representatives, exploiting frustrated travelers by stealing their personal and financial details under the guise of assistance.

Ransomware
A ransomware attack involves hackers encrypting a business’s data and demanding a ransom to restore it. Small tourism operators face significant downtime, lost revenue, and recovery costs if they fall victim to these devastating attacks.
Inbox break-ins
Email compromise attacks are like a break-in to your inbox. Once hackers gain access, they can exploit sensitive information to launch further attacks. In the Qantas Frequent Flyer breach, unauthorised access by overseas contractors led to stolen loyalty points and exposure of personal details, including passport numbers. Such incidents demonstrate how inbox vulnerabilities can lead to significant data theft.
Fake invoices and payment redirection scams
Business email compromise (BEC) fraud often involves fake invoices designed to redirect payments to hackers. These scams are highly convincing, and without careful verification, small businesses can unknowingly send payments to cyber criminals.
Banking burglary
Online banking fraud is another common threat, where cyber criminals gain access to business accounts and transfer money out. These attacks often exploit weak account security measures, emphasising the need for robust protections like long, strong and unique passwords, and multi-factor authentication.

How to stay safe
Cyber security doesn’t have to be complicated, but it does need to be a priority. Protecting your business starts with awareness and taking some simple steps to protect yourself. Train your team to recognise threats and verify communications before acting. Use multi-factor authentication, update your systems regularly, and review all third-party platforms for vulnerabilities.