What are you posting on social media to promote your business today? Are you hyping up a new product, sharing behind-the-scenes footage of a Bali fashion shoot, or launching a flash sale? Social media has become an integral part of small business life in today’s digital age, with clever content helping engage customers and attract new ones. And unfortunately, cyber criminals know it.
Social media hacking incidents are on the rise, and the impact on your bottom line and reputation can be devastating.
The Australian Small Business and Family Enterprise Ombudsman (ASBFEO) reported in May 2024 that the number of cases involving a small business having problems with a digital platform had soared by 127 per cent since July 2022.
Of those, two-thirds were related to Meta, the owner of Facebook and Instagram. In April alone, 75 per cent of those disputes related to accessing an account after being hacked.
But there are some simple steps you can take to help protect against online fraudsters.
Top ways cyber criminals attack your social media business accounts
From dodgy links to fake profiles and even scam funeral pages, there’s no shortage of ways cyber criminals can target you via social media.

The wild popularity of platforms and services such as Facebook, Instagram, LinkedIn, Tik Tok and WhatsApp make them a lucrative target for attackers. Canny cyber criminals cast a wide net to find businesses with weak cyber security processes.
And if your business and personal accounts are connected, it can be even easier for them to sneak through the doors of your business and wreak havoc.
Types of social media attacks include:
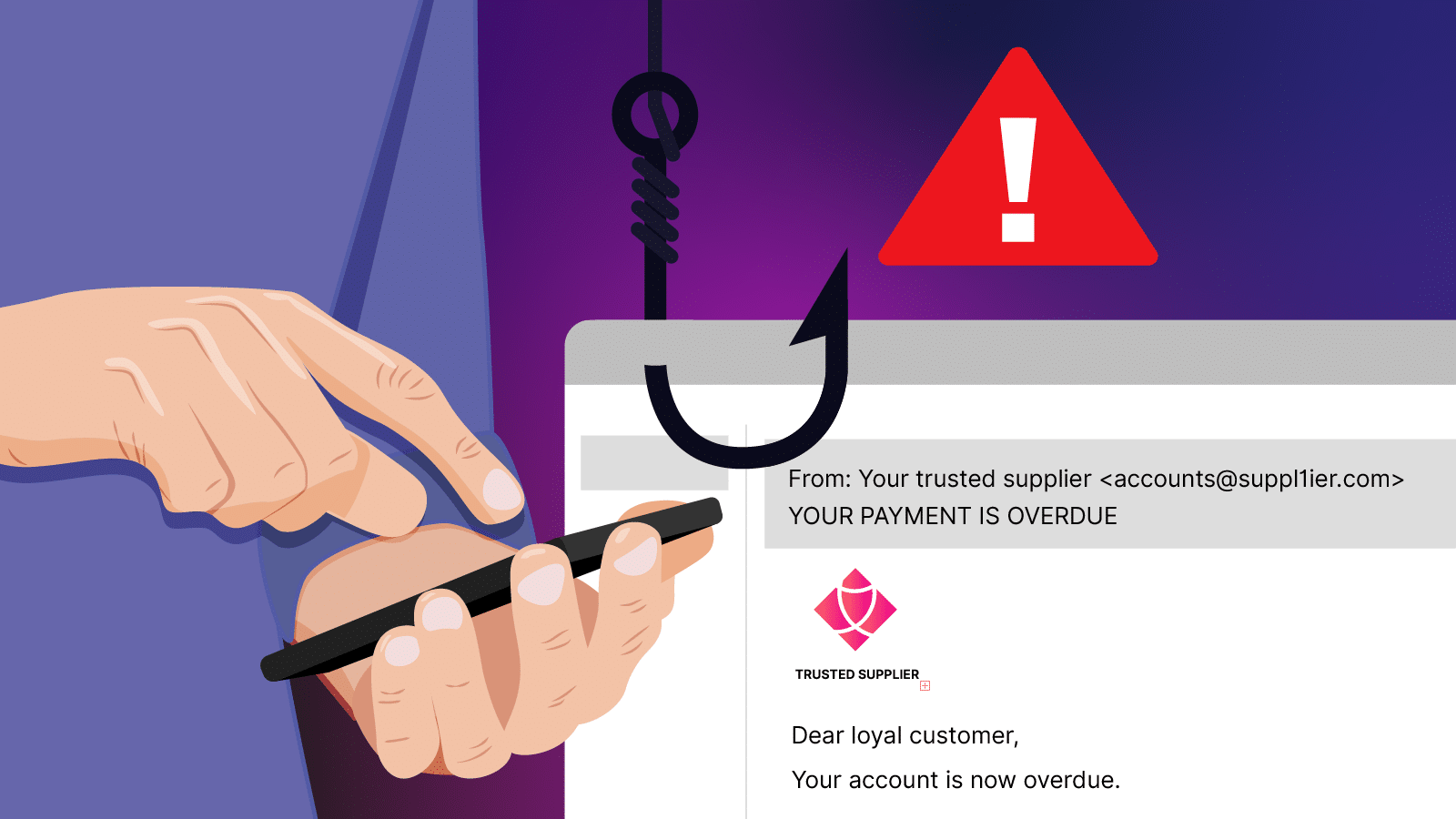
- Phishing: A common social media scam used to try and trick people and businesses into giving away confidential information, such as passwords. Scammers often do this on sites such as TikTok and Instagram by sending fake emails or messages that look official. Or they might impersonate a celebrity or offer prizes. By clicking the link in the message, you are taken to a fake website that prompts you to log in or enter confidential details. The scammer uses that information to access your ccount, putting you and your business at risk of financial loss and identity theft extortion.
- Supply scams: Fake websites and social media pages that are used to sell products that don’t ever arrive.
- Malware: Cyber criminals use malware (short for 'malicious software') to gain access to your information. You might open a link or attachment that downloads malware without you knowing. Some malware may even pose as antivirus or security products.
- “Business Services” or “Meta Services Support” scam: A Facebook Messenger scam with the aim to harvest personal information like usernames and passwords to gain access to online accounts.
A $10,000 lesson on the importance of cyber safety

That was the nightmare that greeted Mimi & Co founder Aami Mills last year, the same day she was due to appear on TV show Shark Tank.
The mother-of-two says the malicious ads featured images such as people fighting and “trying to kill each other”.
“It could not have happened on a worse day, when I was about to go on Shark Tank, and I couldn’t get access to my Facebook or Instagram accounts,” the Canberra business owner recalls.
The budding entrepreneur lost $10,000 to hackers before Facebook was able to take action, and it nearly cost Aami her business.
Aami told ABC News she didn’t have multi-factor authentication on her personal account, only her business account, which the hackers exploited.
“We lost our Facebook page entirely; I still don’t have it back,” she told the news outlet.
“We had to create an entirely new one.
“That was obviously huge for us because we had thousands and thousands of followers but it was something that we had to do.
“It’s kind of a consequence of me not having the right [cyber security measures] in place in the first place.”
Aami has since completed the free Cyber Wardens training which she says was invaluable.
How to protect your social media accounts
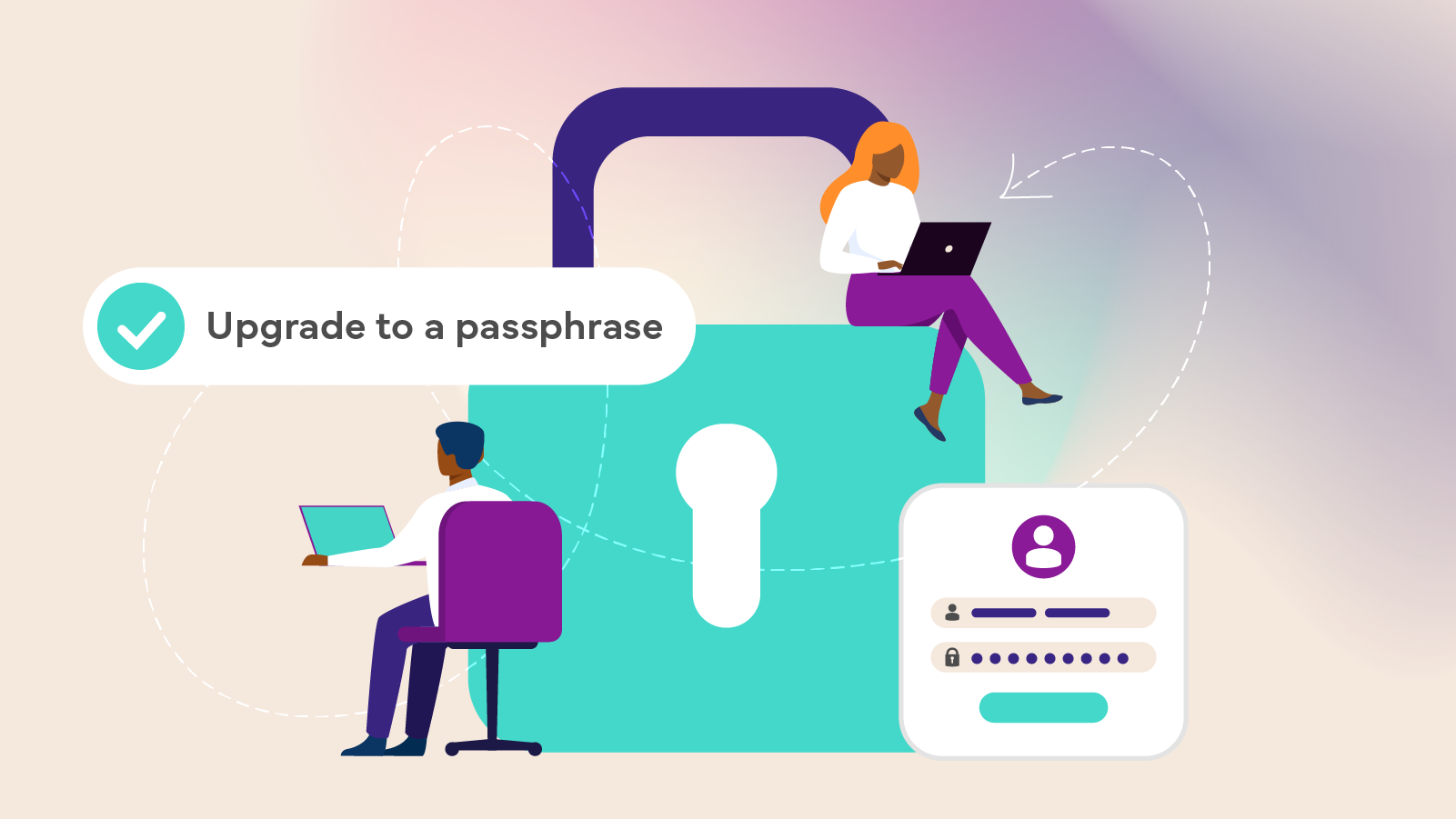
- Use passphrases and password managers: Use strong and unique passphrases for your accounts and consider using a password manager for additional security. Hackers have sophisticated programs to work out passwords, but old-fashioned guessing is still a common way hackers access accounts. That’s why using your pet’s name, your birthday or nickname is never a good idea. Do not allow your devices to remember passphrases for social media accounts, unless stored in a password vault.
- Activate multi-factor authentication (MFA): Always enable MFA for an extra layer of security on your social media accounts. It helps protect your account even if your password is compromised.
- Monitor your devices: Regularly check which devices have access to your accounts. Remove any unfamiliar devices immediately.
- Check for malware: Run antivirus software to detect any suspicious programs on your computer (malware)
- Stay alert to security notifications: Platforms such as TikTok and Facebook monitor for suspicious activity. Regularly check your security alerts for any unrecognised activity.
- Use strong security questions: If asked to set up security questions to recover social media accounts, do not provide answers that could easily be obtained from public sources of information.
- Do your research: The Australian Cyber Security Centre urges businesses to ensure users are aware of processes for regaining control of hijacked social media accounts.
- Keep a low credit card limit: The ASBFEO recommends any credit card linked to a social media account has a limited balance so that if it is compromised, cyber criminals can’t spend too much.
In conclusion
With social media now a critical marketing channel for most small businesses, safeguarding your accounts against cyber criminals is essential to protect your brand, reputation, and customer trust.
From phishing scams to account takeovers, the threats are real, but proactive steps can make all the difference. That’s where the Cyber Wardens program comes in. Designed specifically for small businesses, the program empowers you and your team with the knowledge and tools needed to identify and defend against cyber threats.