Scammers are like criminal pranksters laying traps hoping someone in a small business will fall for one. Except, their pranks aren’t harmless fun.
They are expensive, cost you money, time, and hurt your reputation. The average cost of a cyber attack on a small business has risen to $46,000.
One of their go-to techniques is “impersonation scams” where they pretend to be real people and entities and take advantage of you and your employees.
In 2023 alone (so far), Australians have lost $92 million to impersonation scams this year. In the same period, more than 80,000 reports have been made to Scamwatch — remembering many people don’t report because they feel embarrassed or not sure how to report.
How do impersonation scams work?
According to Scamwatch, most impersonation scams come from text messages, however you should be on the lookout across many channels, including emails and your business social media pages.

One of the ways cyber criminals might approach you or one of your employees include:
- Impersonating the owner or senior leader and asking a colleague to do something for them. They might try to make the employee feel special by saying they’re only asking them because they can trust them or value their work;
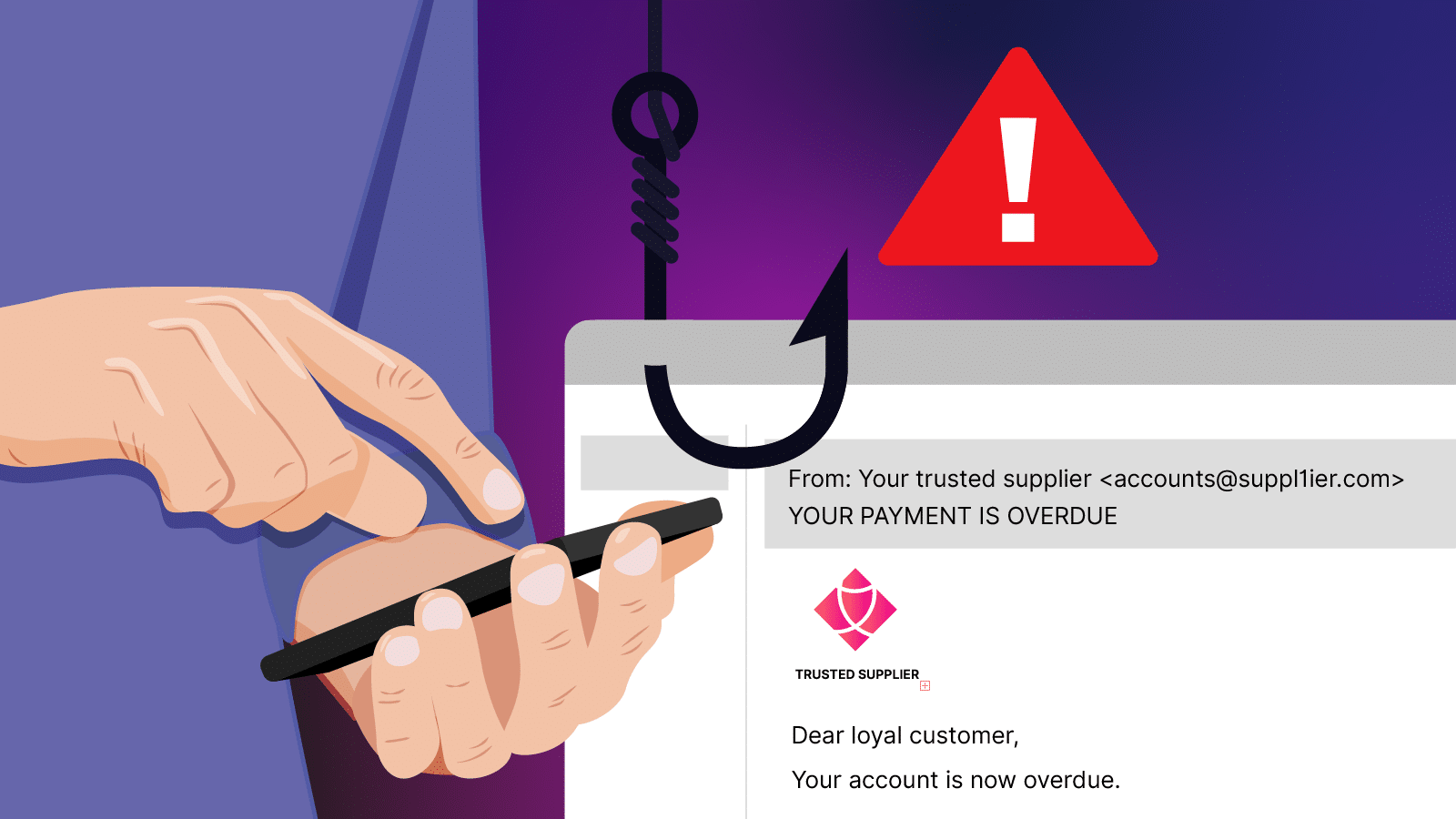
- Impersonating suppliers with fake invoices or saying their bank details have changed;
- Impersonating an unhappy customer by attaching an “image” of a product they’re disappointed in, but this image is actually a different file type — it contains a computer virus;
- Impersonating Facebook/Instagram and saying your business social media page will be shut down if you don’t act on their request.
Cyber criminals never stop looking for cracks in your systems, so it is essential to be aware of what they are looking for and protect yourself and your business from scammers.
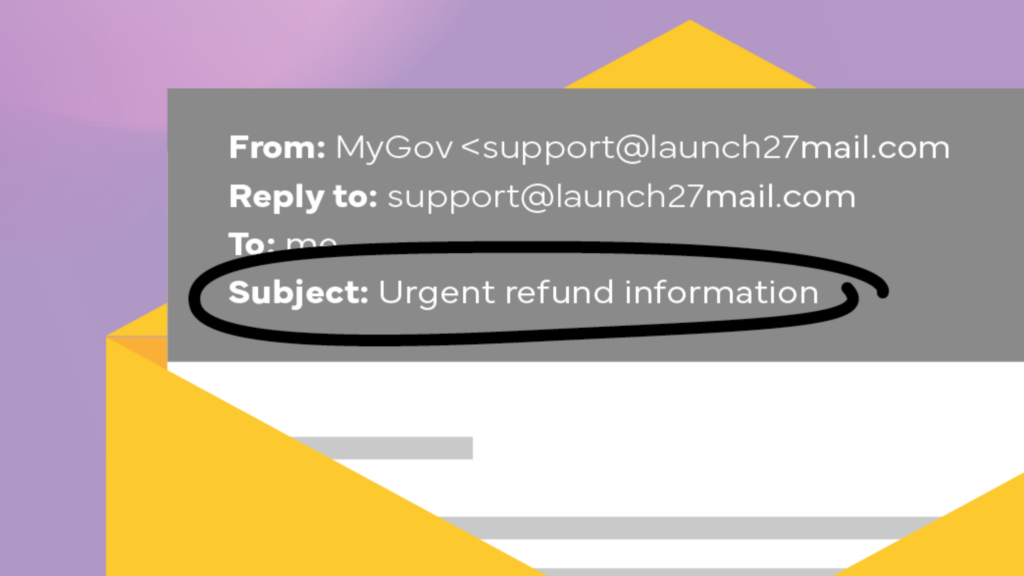
Red Flag #1: Uncommon or misspelt email addresses
Pro tip: Check the email address in the email information bar; it is one you recognise.
Reg Flag #2: Unexpected invoice
Pro tip: Double-check unexpected invoices related to goods or services requested.
Reg Flag #3: Change of banking details for a usual supplier

Pro tip: Confirm invoice details directly with suppliers using a trusted contact number. Not the phone number found on the suspicious invoice.
Reg Flag #4: Unusual requests
Pro tip: Follow your normal payments process and review suspicious requests with a teammate. Ask your accountant or a trusted friend for help if you are a sole trader.
Reg Flag #5: Pressure to act urgently or confidentially
Pro tip: Scammers may target you when your business is known to be busy, such as during Christmas sales. Go slow and review the requests.
Reg Flag #6: Unusual or hidden links
Pro tip: Banks and governments will never ask you to click on a link.
Red Flag #7: Suspicious attachments on emails or social media messages
Pro tip: Double-check the file type before you download an attachment. Unsolicited requests to open or download attachments can hide dangerous malware.
You can enrol in our free cyber training to gain even more insights and skills to help protect yourself and your small business.